Maria Harika, James Hubner, Mitchell Riggan, Joseph Green
Introduction
On 09JAN2026, Scattered LAPSUS$ Hunters (SLSH) leaked a BreachForums (BF) user database
containing over 320,000 user records on their Dedicated Leak Site (DLS). While the dataset was
publicly released in JAN2026, analysis indicates the data originates from a breach that
occurred in OCT2025. The JAN2026 leak is a high profile resharing of the same compromised
database, rather than a newly obtained intrusion. Several notable actors tracked by our team
and the community appear in the leak, providing new visibility into their forum presence,
aliases, and activity patterns.
BreachForums
Launched in 2022, BreachForums served as the successor to RaidForums. The platform
became the most prominent English language cybercrime forum and facilitated the trading of
stolen data, selling hacking tools and network access, distributing malware, coordinating
ransomware activity, and hosting fraud and credential marketplaces.
The forum became a frequent target for law enforcement operations, internal leaks, and rival
threat actors. After the arrest of founder Conor Brian Fitzpatrick (“pompompurin”) in 2023, the
forum went through multiple ownerships and admin changes. Control ran through various
threat actors/groups like ShinyHunters, IntelBroker, and admins using the alias “Anastasia.”
Brief BreachForums timeline:
➔ MAR2022: BreachForums launched by pompompurin as successor to RaidForums
➔ MAR2023: pompompurin arrested; forum temporarily down
➔ Mid-2023: Forum relaunched under new admin, including ShinyHunters
➔ 2024: Admin shifts to the alias “Anastasia”
➔ Early 2025: IntelBroker assumes control; later arrested that year
➔ OCT2025: US and French authorities seize BreachForums related domains tied to extortion activity
➔ 09JAN2026: database linked to BreachForums is leaked by a site associated with ShinyHunters exposing user accounts, private messages, and admin data.
Scattered LAPSUS$ Hunters (SLSH)
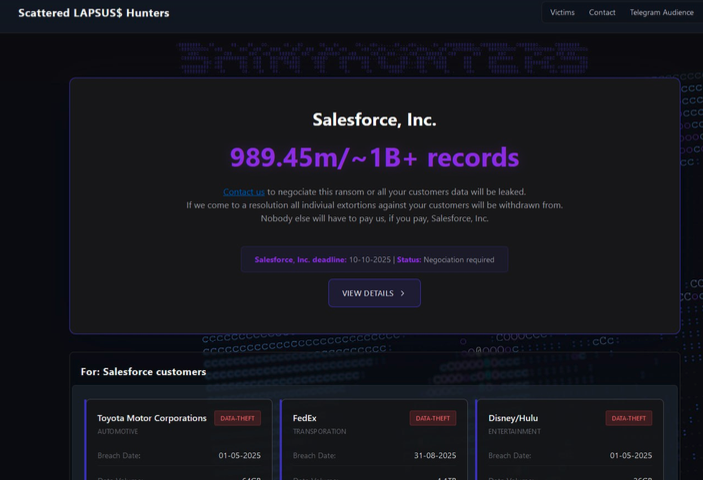
Scattered LAPSUS$ Hunters (SLSH) is a cybercriminal collective formed in mid-2025, including members from Scattered Spider, LAPSUS$, and ShinyHunters for coordinated extortion and data theft operations. The group focuses on coordinated extortion and data theft operations, targeting high profile organizations and technology platforms.
SLSH has operated multiple Telegram channels and a Dedicated Leak Site (DLS) to publish breaches claims, victim lists, and stolen data. The group initially gained attention for the compromises involving SaaS platforms and Salesforce related environments..
The Breach: What was Exposed
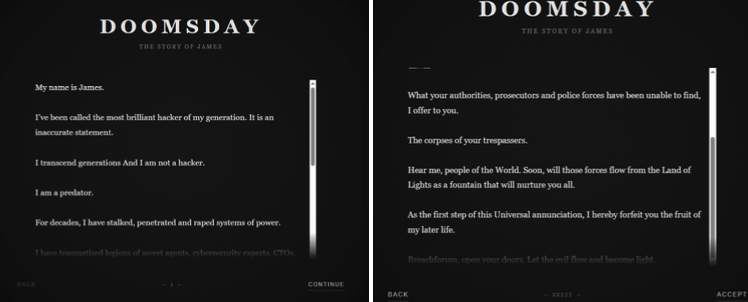
On 09JAN2026, the SLSH DLS shinyhunte[.]rs surfaced with a page titled “Doomsday: The Story of James,” which takes users to download a BreachForums database archive.
The below images reflect the most recent update to the shinyhunte[.]rs domain, which previously hosted content related to the Salesforce leak.
After navigating through approximately 23 pages of narrative text, users are presented with a direct link to a compressed 7z archive. After accepting and downloading the file, the archive was found to contain:
➔ A text document mirroring content posted on the website
➔ The BreachForums PGP Secret key
➔ A SQL database export containing forum user records, including credentials, emails, and account metadata.
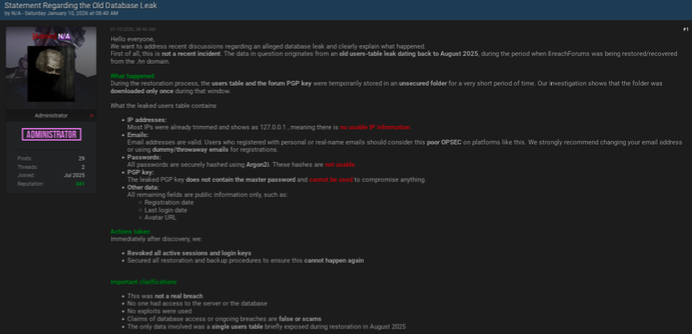
Current BreachForums administrators claim the leaked data was partial and dated back to mid-2025. DarkTower analysis supports this assessment, indicating the database content aligns with forum activity and records consistent with the OCT2025 breach window.
The data exposure likely occurred during a period when BreachForums was being restored or recovered under its former .hn domain. During this process, the user table and forum PGP key appear to have been placed in an unsecured directory, allowing unauthorized access and exfiltration. The JAN2026 leak represents the public redistribution of this previously compromised dataset.
Exposed Threat Actors
Analysis of the BreachForums dataset confirms the presence of multiple known high profile data leakers, hacktivists, ransomware affiliates, etc. The following examples are the types of actors identified within the dataset:
Loki (BreachForums Moderator)
Loki’,’$argon2i$v=19$m=65536,t=4,p=1$SkFUR3ZJOXZ2Q1V2cURxWQ$4rhfA1rZy141cKTvmOwZ2ipkzXUuhvkHY6tgCbhgrk8′,’Y8PU2Q0X’,’xodLICJaraV9phfbUug52DJO5jddoq6IVdtUm6vlNg6zPtAq6v’,’certifiednigger@memeware.net’,2451,64,’./uploads/avatars/avatar_229941.jpg?dateline=1724621360′,’300|400′,’upload’,3,”,415,’The God of Stories’,1719738914,1754913040,1754907828,1754911696,”,’0′,”,”,”,’all’,'[img]https://64.media.tumblr.com/c28f803dbfef10a302ff051a43746f2f/3c5cd0a36f0a9b03-5f/s540x810/e47c91a87cc521d1efbd20183b42ee4259c9c593.gifv[/img]\r\n[url=https://pastebin.com/yjgXNNUB]PGP[/url]’,0,1,0,1,1,0,2,0,1,0,”,1,1,1,1,1,1,0,0,0,’0′,’0′,’0′,0,2,”,”,0,0,0,’0′,”,’0$%%$1$%%$2$%%$3$%%$4**’,”,0,6,1787,0x7F000009,0x7F000009,”,2371165,1,353,4,0,0,0,0,0,0,0,0,0,1,0,”,0,588.00,’argon2i’,0,”,'[]’,”,0,’0′,”,’a:1:{s:7:\”session\”;s:66:\”057a36bb51f17c3d4dd59950eaf83103939dfc411b387f25a38f8b13b8b256f47a\”;}’,1,0,0,0,”);
888 (BreachForums Moderator)
(25923,’888′,’$argon2i$v=19$m=65536,t=4,p=1$VC5hQUtBZXNrZ1JBbVU1TA$4PmWNWclDHvBTpQx/ItlB2788pdFQm7tk8umjfYqxwU’,’maSfX4EA’,’vg30NEy9AXEL8z5rgT6XHrmBwy6PkVAuhfFrV8WIKWANVTMMmo’,’theCleanSt4tue@airmail.cc’,1004,131,’./uploads/avatars/avatar_25923.jpg?dateline=1735568083′,’296|400′,’upload’,6,”,330,’Kingpin’,1692376533,1754953804,1754952050,1754933963,’https://doingfedtime.com/888/’,’0′,”,”,”,’all’,'[align=center][img]https://external-content.duckduckgo.com/iu/?u=http://pomf2.lain.la/f/l0xgkt9q.gif[/img][/align]\r\n[align=center]@IntelBroker @EnergyWeaponUser @888 @wonder[/align]\r\n[align=center][url=https://pastebin.com/raw/iL4mecAg]PGP[/url][/align]\r\n’,1,0,0,1,1,0,1,0,1,0,”,1,1,1,1,1,1,0,0,0,’0′,’0′,’0′,1,2,’17170′,”,0,0,0,’0′,”,’0$%%$1$%%$2$%%$3$%%$4**’,”,0,12,4159,0x7F000009,0x2D813B44,”,3907990,1,61,0,0,0,0,0,0,0,0,0,0,1,0,”,0,11744.00,’argon2i’,0,”,'[]’,”,0,’0′,”,’a:3:{s:7:\”keybase\”;s:7:\”real888\”;s:6:\”matrix\”;s:20:\”@bullying:matrix.org\”;s:7:\”session\”;s:66:\”054de8cc127c76f94eed19bbcc950fe9c9f6f9ef9f410f79e64989f480197a4476\”;}’,0,0,0,0,”);
NarodArmiya (BreachForums Moderator)
(471230,’NarodArmiya’,’$argon2i$v=19$m=65536,t=4,p=1$MEhHNG43eHJhWFpqSkE5SA$hF4fuWfkM9DeTPY3I7aA/6JfMJz0u+rgcJox0zyRrjk’,’jH0GnDR7′,’5nCcJHVQspSupSU6LcSskl2XAw6r2fR51Mfmopdb2ELNGXI3iC’,’TCMSecurity@proton.me’,176,28,’./uploads/avatars/avatar_471230.jpg?dateline=1754488561′,’400|400′,’upload’,8,”,631,’⭐⭐ Народная CyberАрмия ⭐⭐’,1753685113,1754930837,1754923815,1754914701,”,’0′,”,”,”,’all’,'[color=#c10300]Session:[/color] [b][color=#008e02][u]059948f695d926899bb5fdb130a1d1de16f919c4a0fb7432d2c323d799d07cd811[/u][/color][/b]\r\n[color=#c10300]qTox:[/color][color=#008e02] [u][b]4CBAF7F9EF8253BF8AC088A949778250DD305EB0D8414AD847E617B6C848752DF0940CACCE24[/b][/u][/color]’,1,1,0,1,1,0,2,0,1,0,”,1,1,1,1,1,1,0,0,0,’0′,’0′,’0′,0,0,”,”,0,0,0,’0′,”,’0$%%$1$%%$2$%%$3$%%$4**’,”,0,0,421,0x7F000009,0x7F000009,”,251583,1,13,1,0,0,0,0,0,0,0,0,0,1,0,”,0,33.00,’argon2i’,0,”,'[]’,”,0,’0′,”,’a:2:{s:4:\”qtox\”;s:76:\”4CBAF7F9EF8253BF8AC088A949778250DD305EB0D8414AD847E617B6C848752DF0940CACCE24\”;s:7:\”session\”;s:66:\”059948f695d926899bb5fdb130a1d1de16f919c4a0fb7432d2c323d799d07cd811\”;}’,0,0,0,1,”);
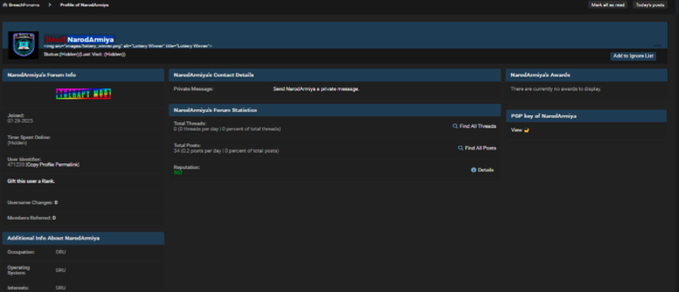
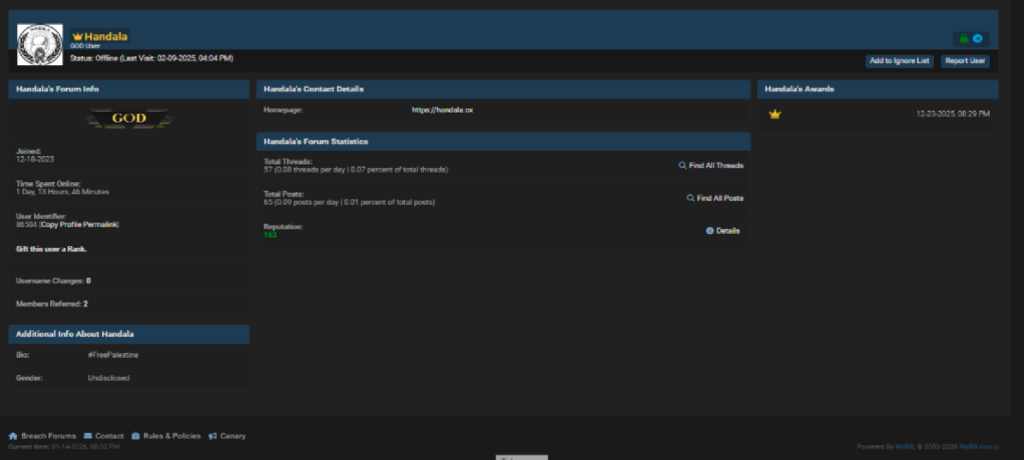
Handala (Hacktivist)
(86504,’Handala’,’$argon2i$v=19$m=65536,t=4,p=1$NDUuNFFqSDEzTW9tQ0dDVg$fj9SCgj8XVoEdMsbqUJsg69bbPyfChd8RQVzdiVpnxQ’,’sndk735l’,’JRsy3q2IMPil5a3b9ktJZt2DW01DuhMKkOrMcuTM4g7SrQDwry’,’handala2024@proton.me’,65,57,’./uploads/avatars/avatar_86504.jpg?dateline=1702889629′,’400|400′,’upload’,8,”,0,”,1702889514,1739117076,1739089494,1739117050,’https://handala.cx’,’0′,”,”,”,’all’,”,1,1,0,0,0,0,0,0,1,0,”,1,1,1,1,1,1,0,0,0,”,”,’0′,0,2,”,”,0,0,0,’0′,”,’0$%%$1$%%$2$%%$3$%%$4**’,”,0,2,163,0x7F000009,0x7F000009,”,135963,1,0,0,0,0,0,0,0,0,0,0,0,1,0,”,0,154.00,’argon2i’,0,”,'[]’,”,0,”,”,’a:2:{s:4:\”qtox\”;s:76:\”02C75E60211314F4A69C323A3CE334D75C72CD8C742F3ED168447405C541DF057294365D6C1E\”;s:8:\”telegram\”;s:14:\”Handala_Backup\”;}’,0,0,0,0,”);
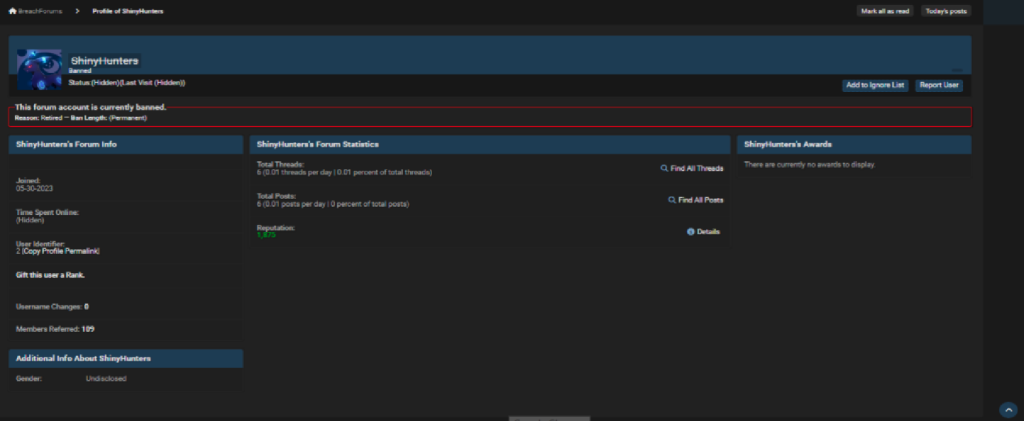
ShinyHunters
(2,’ShinyHunters’,’$argon2i$v=19$m=65536,t=4,p=1$V0tDNWdGVk9ENlo2aVBWVQ$e5RpG8afJds8HA6mkVehErnC+tqlUr8CVH6EPJa93ZU’,’0aD4YjHd’,’DBydbBlDLNThW9vB7PjZnra95YR2x3ffa8bk0UrTDomNRo7AAZ’,’vinnyhunter@pokemon.com’,9,9,’./uploads/avatars/avatar_2.jpg?dateline=1716924433′,’400|400′,’upload’,12,’328′,4,”,1685485743,1754933007,1754930993,1754923096,”,’0′,”,”,”,’all’,’PGP: https://pastebin.com/raw/qUp9Ax9M\r\nPGP Archive Link: https://web.archive.org/web/20210921111301/raidforums.com/user-ShinyHunters’,0,1,0,1,1,0,2,0,1,0,”,1,1,1,1,1,1,0,0,0,’0′,’0′,’0′,0,0,”,”,0,0,0,’0′,”,’0$%%$1$%%$2$%%$3$%%$4**’,”,0,107,1894,0x7F000009,0xB95D03C3,”,951795,1,16,1,0,0,0,0,0,0,0,0,0,1,0,”,0,3250.00,’argon2i’,0,”,'[]’,”,0,’0′,”,’a:0:{}’,0,1,0,0,”);
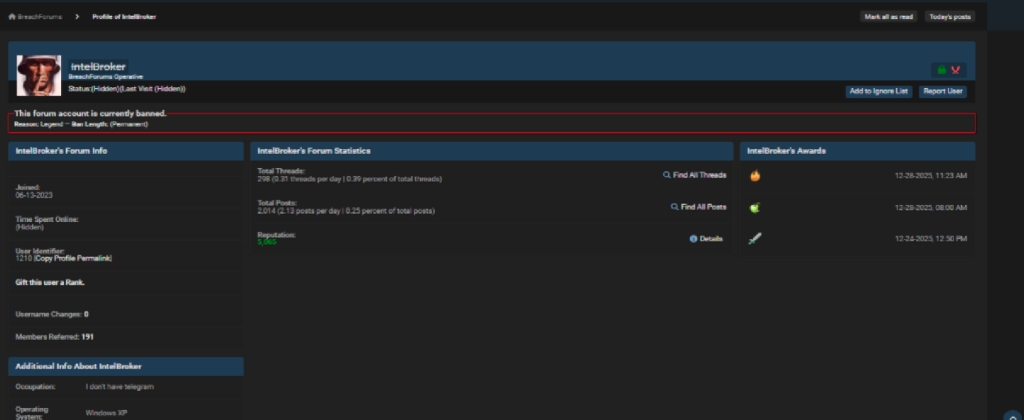
IntelBroker
(1210,’IntelBroker’,’$argon2i$v=19$m=65536,t=4,p=1$ZnJqLjVReW0yNm1WUTlLcA$I8VmyFHD9rWslTc5rKsFp3VNhA8CbWSpdfbn6axYMKI’,’zpUCbn0A’,’qvCB8hGqqkQsO58087Y8865ai2irQfEE35G3QnWVFCKjQ4W9P7′,’intelbroker@national.shitposting.agency’,2039,301,’./uploads/avatars/avatar_1210.png?dateline=1737669509′,’236|239′,’upload’,7,”,0,’BreachForums Operative’,1686679770,1741001350,1741001338,1738881167,”,’0′,”,”,’29-7-1998′,’age’,'[align=center][img]http://pomf2.lain.la/f/l0xgkt9q.gif[/img][/align]\r\n[align=center]@IntelBroker @EnergyWeaponUser @Wonder @888[/align]\r\n’,0,1,0,1,1,0,0,0,0,1,”,1,1,1,1,1,1,0,0,0,’0′,’2′,’3′,0,2,”,’64690′,0,0,0,’0′,”,’0$%%$1unread$%%$2sent items$%%$3$%%$4$%%$8’,”,0,188,5064,0x7F000009,0x7F000009,”,3919946,1,1,1,0,0,0,0,0,0,0,0,0,4,0,”,0,4470.00,’argon2i’,0,”,'[2,3,7,8]’,”,0,’0′,”,’a:2:{s:4:\”qtox\”;s:76:\”C400C2E637A3A7AFE7FD137841793245963A71D64CBA95B3F5057C2860FEDA273136950EB87A\”;s:4:\”xmpp\”;s:27:\”intelbrokerbf@thesecure.biz\”;}’,1,1,0,0,”);
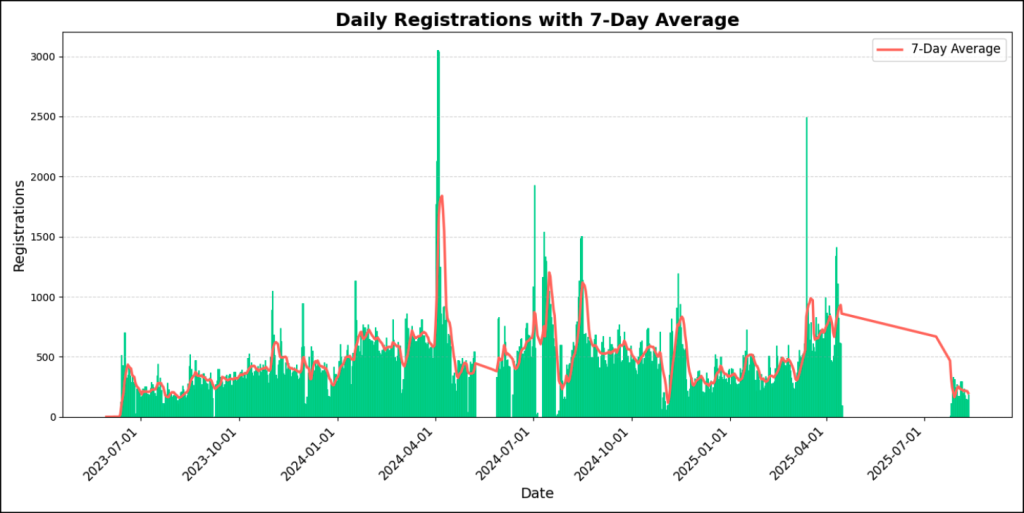
Registration Timeline
DarkTower analyzed the BreachForums registration data and identified several spikes that closely align with major breach disclosures and forum related disruptions.
The first major increase occurred in early APR2024, coinciding with the National Public Data breach posting. Between 02APR2024 and 04APR2024, the forum recorded 6,088 new registrations, representing the largest single surge in user registrations. The second notable spike occurred in MAR2025, coinciding with the Oracle breach posting. On 13MAR2025, the forum recorded 2,495 new registrations.
Overall, registrations increased following high-profile breach disclosures and frequently paused or declined following law enforcement actions or forum takedowns.
Geographic Distribution
When DarkTower analyzed the geographic distribution of BreachForums users, based on both registration IP addresses and last known login IPs, the data revealed a globally diverse user base with concentrations across North America, Europe, and parts of Asia.
The registration IPs reflect the location at account creation, whereas last login IPs reflect more recent access patterns. Any difference between the registration and last login locations might point to uses of VPNs or proxies.
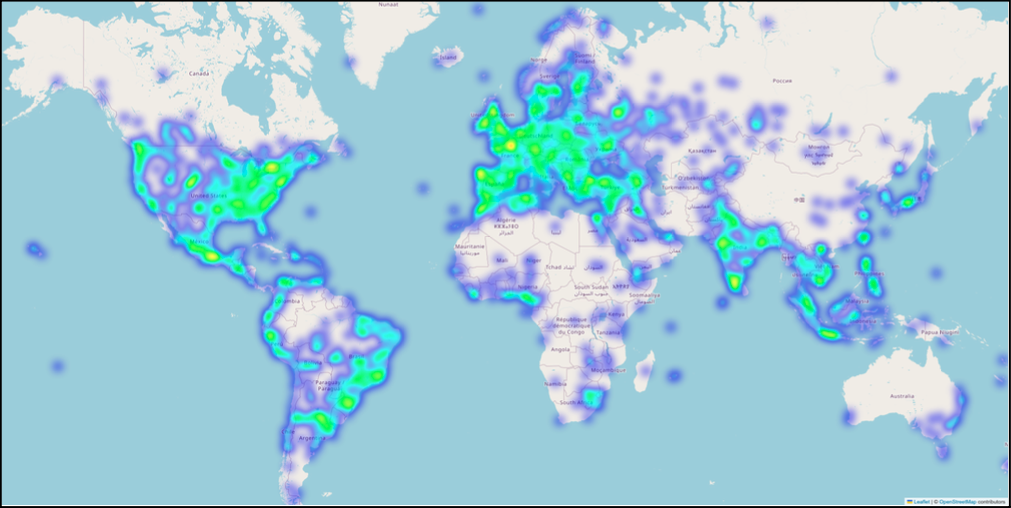
Last IP login
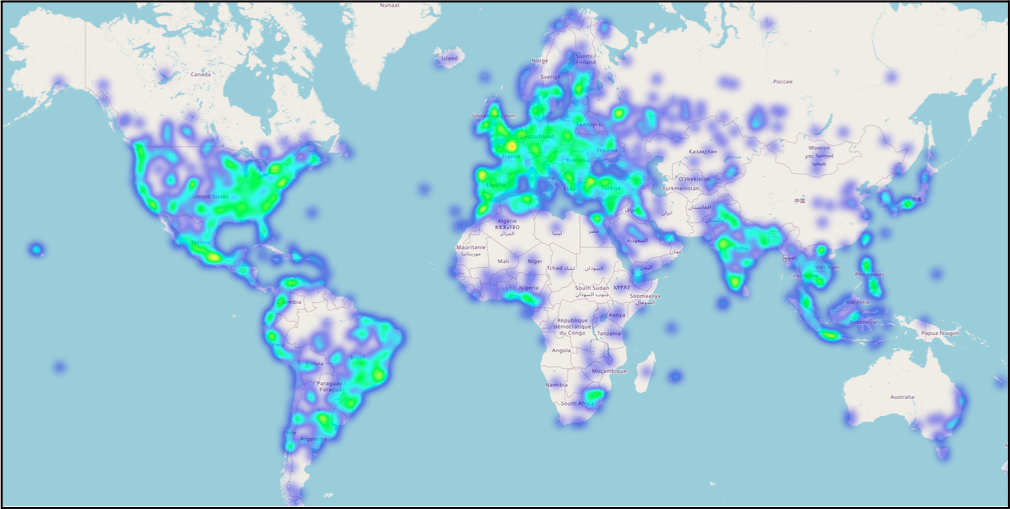
Registration IP
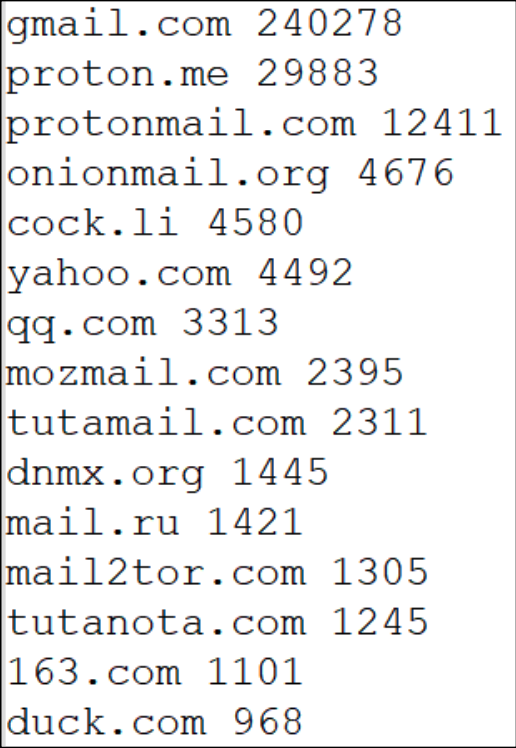
Email Domain Usages
DarkTower analysis of email domain usage shows that Gmail was the most commonly used provider by a wide margin, accounting for over 240,000 registrations. Proton, the second most used, accounted for more than 42,000 registrations.